40 an rfid label on a box is an example of what type of physical security detection method
SOLICITATION PROVISIONS AND CONTRACT CLAUSES - Acquisition (3) Apply other information systems security measures when the Contractor reasonably determines that information systems security measures, in addition to those identified in paragraphs (b)(1) and (2) of this clause, may be required to provide adequate security in a dynamic environment or to accommodate special circumstances (e.g., medical ... Network+ 8th Edition Chapter 9, Network+ Flashcards - Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper ...
Ch9 network Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. On a Linux based system, what command can you use to create a hash of a file using SHA-256? ...

An rfid label on a box is an example of what type of physical security detection method
Ch 9: Network Risk Management Flashcards Preview - Brainscape An RFID label on a box is an example of what type of physical security detection method? A asset tracking tagging 20 Q What statement regarding the different versions of the SHA hashing algorithm is accurate? A SHA-2 and SHA-3 both support the same hash lengths. 21 Q Network+ 8th Edition Chapter 11, Chapter 10 ... - Quizlet When using DiffServ, what type of forwarding utilizes a minimum departure rate ... An RFID label on a box is an example of what type of physical security ... Chapter 9 -- Network II Flashcards | Quizlet A) Polymorphic malware can change its characteristics every time it is transferred to a new system. B) Polymorphic malware is designed to activate on a particular date, remaining harmless until that time. C) Polymorphic malware is software that disguises itself as a legitimate program, or replaces a legitimate program's code with destructive code.
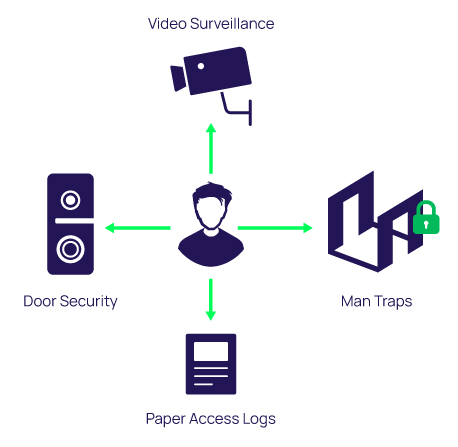
An rfid label on a box is an example of what type of physical security detection method. Ch. 9 Quiz CTS1134 Flashcards - Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. How do RFID and RF tags work? - Explain that Stuff Photo: An example of the kind of RFID tag used in book labels. It helps with automated stock control and (in some systems) might double-up as an anti-theft device. You can often see these by holding library paperbacks up to the light. This tag is a UPM Raflatac RaceTrack that can hold up to 1 kilobyte (1024 characters) of information. THE RFID TECHNOLOGY AND ITS APPLICATIONS: A REVIEW - ResearchGate Radio frequency identification (RFID) technology is an automatic recognition system that uses radio waves to identify products and objects. RFID system consists of a tag, a reader, and a ... What is Physical Security? Measures, Best Practices + PDF Guide Physical security is always a component of a wider security strategy, but it makes up a sizeable piece of this larger plan. Security experts agree that the three most important components of a physical security plan are access control, surveillance, and security testing, which work together to make your space more secure.
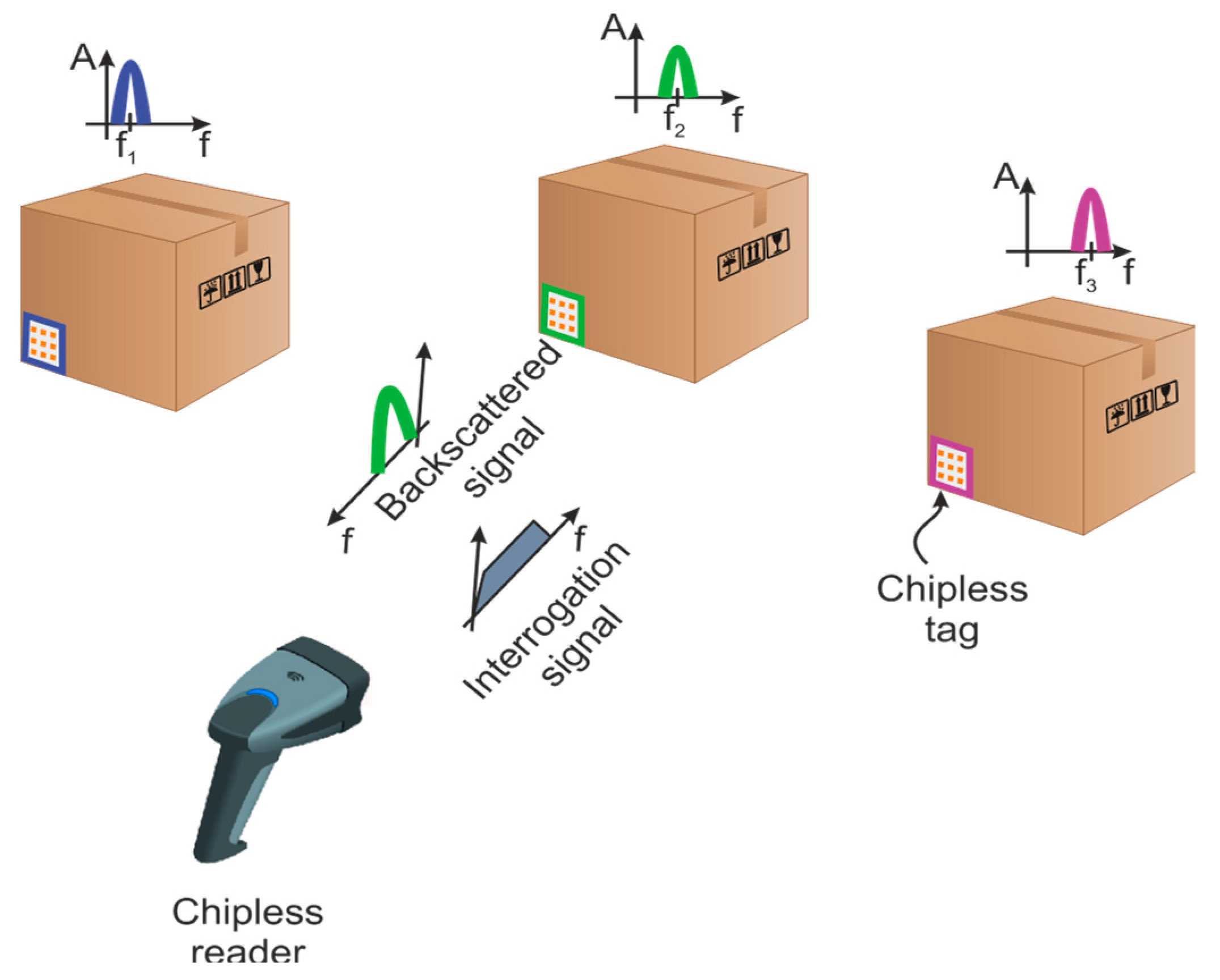
Networking, Chapter 9 Quiz Flashcards | Quizlet "An RFID label on a box is an example of what type of physical security detection method? video surveillance via CCTV * tamper detection Radio-frequency identification - Wikipedia Often more than one tag will respond to a tag reader, for example, many individual products with tags may be shipped in a common box or on a common pallet. Collision detection is important to allow reading of data. Two different types of protocols are used to "singulate" a particular tag, allowing its data to be read in the midst of many ... Chapter 9 Questions Flashcards - Quizlet The original version of the Secure Hash Algorithm was developed by MIT. ... An RFID label on a box is an example of what type of physical security detection ... Credit card - Wikipedia Additionally, there are security features present on the physical card itself in order to prevent counterfeiting. For example, most modern credit cards have a watermark that will fluoresce under ultraviolet light. Most major credit cards have a hologram. A Visa card has a letter V superimposed over the regular Visa logo and a MasterCard has the ...
What Is RFID Technology and How Can I Use It? - Shopify RFly, for example, created a drone that scans RFID tags and locates products inside a warehouse. If the item is stacked on a high shelf, the drone will collect it. With RFID-enabled drones, the health and safety risks of a factory worker are diminished. There's no need for them to use machinery or climb ladders to retrieve the item. Postal Terms - USPS Each box is secured with special security lock called an arrow lock. The box has a uniform appearance and a nationwide identification system that shows USPS logo, type of service, and collection times provided at each box. In addition to the standard size box, there are larger boxes for high-volume areas, a Priority Mail Express box, and a ... What are RFID Tags, How Do They Work? - Camcode RFID tags are a type of tracking system that uses smart barcodes in order to identify items. RFID is short for "radio frequency identification," and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program. Network+ 8th Edition Chapter 9 Updated Flashcards - Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper ...
US7360714B2 - Label and RFID tag issuing apparatus - Google A label and RFID tag issuing apparatus comprises a recording apparatus that records information on a production label and an RFID tag reader/writer that writes and reads part of the recorded information to/from an RFID tag. This label and RFID tag issuing apparatus writes a production number to the RFID tag attached to the container if a container for containing an article or articles carrying ...
Networking 5 | Networking Quiz - Quizizz An RFID label on a box is an example of what type of physical security detection method? answer choices . tamper detection. motion detection technology. video surveillance via CCTV. asset tracking tagging. Tags: Question 28 . SURVEY .
US20070199988A1 - Method and means for detection of counterfeit items ... This invention relates to the use of radio frequency identification (RFID) tags and labels, as a means of preventing and/or detecting counterfeiting in the fashion, jewelry, timepiece, art, luxury goods and wearable accessory industries and the authentication of bona fide articles and/or their owners. ... Method and means for detection of ...
Radio Frequency Identification (RFID) | FDA The reader is a device that has one or more antennas that emit radio waves and receive signals back from the RFID tag. Tags, which use radio waves to communicate their identity and other...
RFID Programming: Easy Guide for Beginners | Developer.com The RFID Hardware. RFID generally involves a reader and a set of tags. The reader scans a tag and pulls information from it. This information can be used to uniquely identify the tag and thus identify whatever is associated to the given tag. There are a variety of readers that can be used. These range from readers for passive tags to readers ...
Federal Register :: Remote Identification of Unmanned Aircraft Jan 15, 2021 · Label the unmanned aircraft or remote identification broadcast module to indicate that it is remote identification compliant. Submit a declaration of compliance for acceptance by the FAA, declaring that the standard remote identification unmanned aircraft or remote identification broadcast module complies with the requirements of the rule.
How is a posture assessment performed on an - Course Hero An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging What statement regarding the different versions of the SHA hashing algorithm is accurate? a.
US20180157873A1 - Process for rfid certification of carton content ... A process for RFID certification of carton content. Cartons may be packed with a number of RFID-tagged items and sealed. A carton may then be placed in the proximity of a scanner, which may verify the number and type of items present in the container. The carton ID information and measured RFID data of the carton contents may then be compared to a database, and an RFID pack certification label ...
Gadgets • TechCrunch 2 days ago · Read the latest news, updates and reviews on the latest gadgets in tech. Coverage includes smartphones, wearables, laptops, drones and consumer electronics.
Linux kvm citrix xenserver correct correct vmware 2 / 2 ptsquestion 36 an rfid label on a box is an example of what type of physical security detectionmethod? asset tracking taggingcorrect!correct! motion detection technology video surveillance via cctv tamper detection 2 / 2 ptsquestion 37 an attack that relies on redirected and captured secure transmissions as they occur is known as what type …
US20060214789A1 - Tamper detection with RFID tag - Google A sensor may be used to detect a previous or current change of state, and the change may be reported by a radio frequency identification (RFID) tag. In some embodiments, the change may represent a broken security seal, which in turn may affect an electrical connection that can be sensed by the RFID tag during operation of the RFID tag.
Question28 11pts what type of door access control is - Course Hero key fob lock Question 29 1 / 1 pts An RFID label on a box is an example of what type of physical security detection method? Correct! asset tracking tagging video surveillance via CCTV tamper detection motion detection technology asset tracking tagging
Ch. 9 Quiz CTS1134 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised
Network+ 8th Edition Chapter 9 Flashcards | Quizlet A virus that remains dormant until a specific condition is met, such as the changing of a file or a match of the current date is known as what type of malware? a. encrypted virus b. logic bomb c. boot sector virus d. worm b. logic bomb 11. An RFID label on a box is an example of what type of physical security detection method?
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging asset tracking tagging 12.
8.docx - 39. With VTP, where is the VLAN database stored?... An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging44. An attack that relies on redirected and captured secure transmissions as they occur is known as what type of attack? man-in-the-middle attack 45. How often should you require users to change their passwords? every 60 days 46.
Free Computers Flashcards about Chap 9 and 10 Quiz - StudyStack An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging: What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths.
Artificial intelligence - Wikipedia Knowledge representation and knowledge engineering allow AI programs to answer questions intelligently and make deductions about real-world facts.. A representation of "what exists" is an ontology: the set of objects, relations, concepts, and properties formally described so that software agents can interpret them.
PDF Guidelines for securing Radio Frequency Identification (RFID ... - GovInfo information technology. ITL's responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. Special Publication 800-series
What is RFID? | The Beginner's Guide to How RFID Systems Work An RFID inlay or label is a common example of a recurring cost in an RFID system. Because of their low-cost, these tags are frequently applied once and kept on an item for its lifespan (or discarded after use). If an RFID printer is used, then printer ribbon would also be a recurring cost.
Exam 5 CIS 330, Ch 9, Network+ 8th Edition Chapter ... - Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging.
27how is a posture assessment performed on an 29.An RFID label on a box is an example of what type of physical security detectionmethod? asset tracking tagging asset tracking tagging 30.What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. SHA - 2 and SHA - 3 both support the same hash lengths .
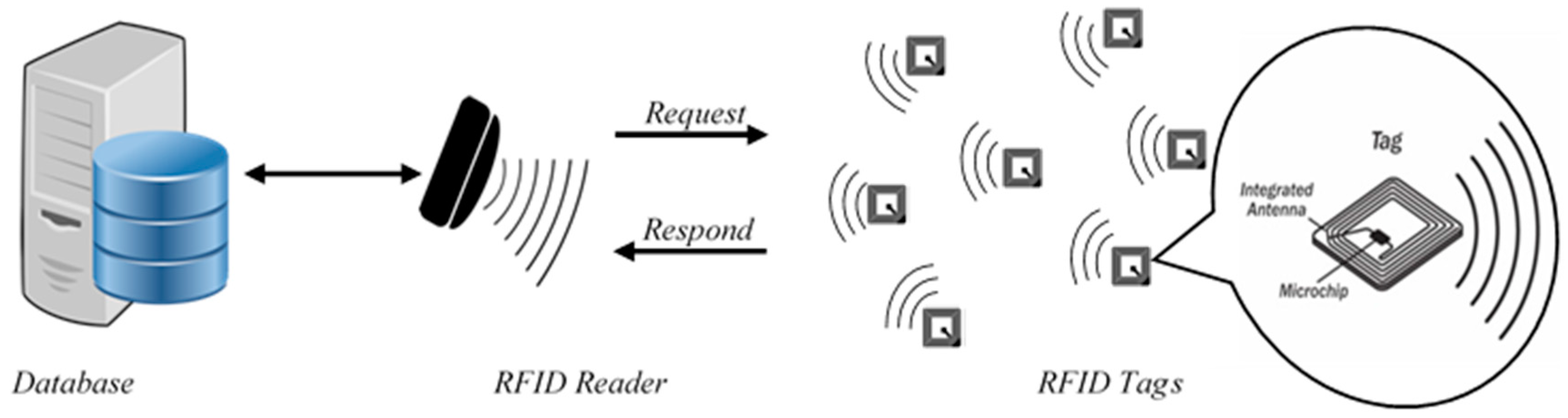
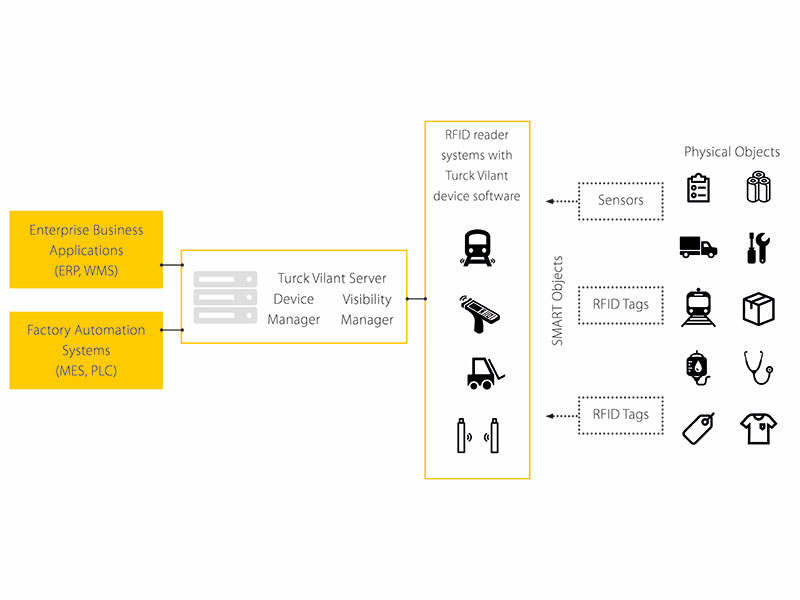
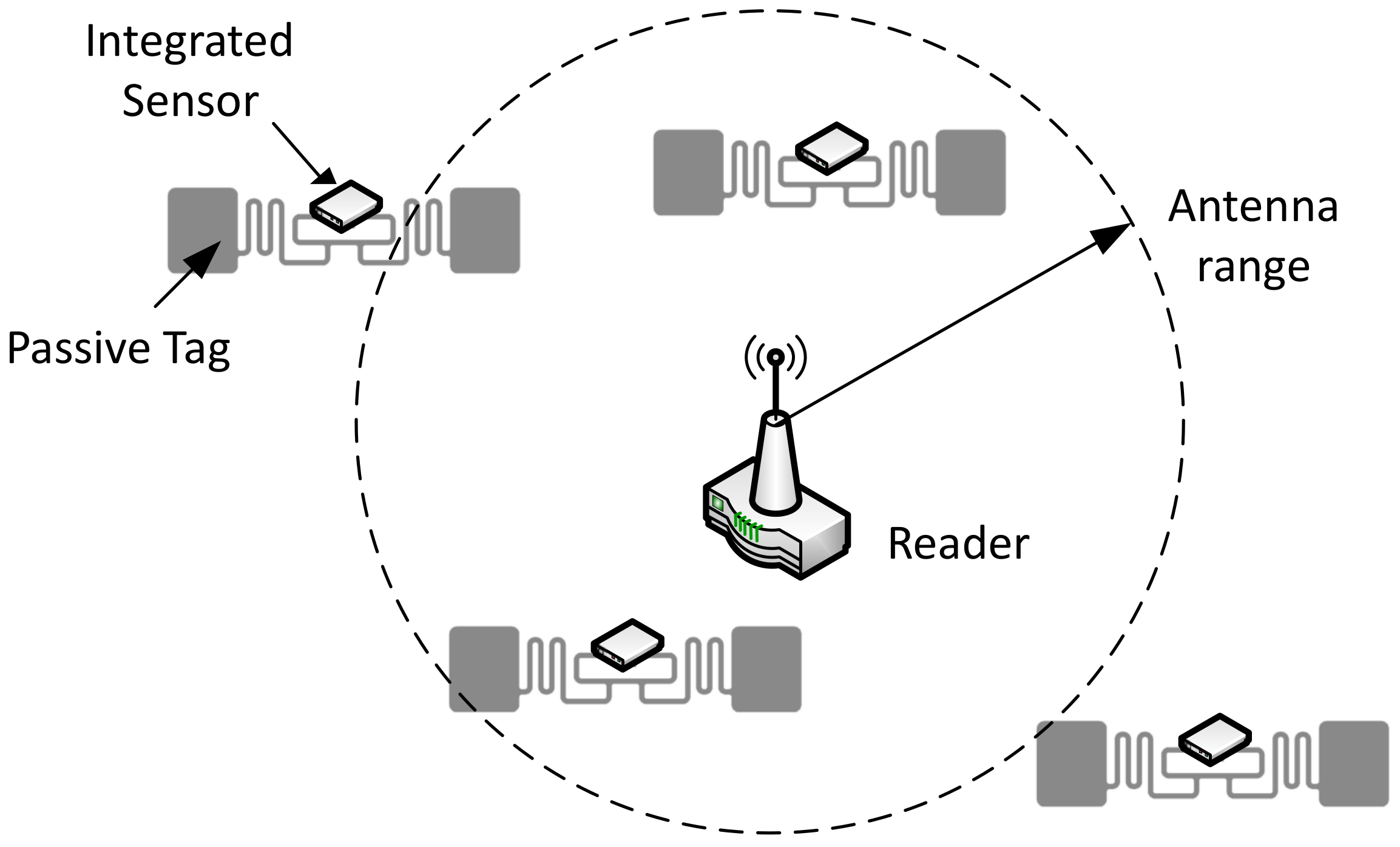
RFID methods utilize radio waves to accomplish this. At a simple level, RFID systems consist of three components: an RFID tag or smart label, an RFID reader, and an antenna. RFID tags contain an integrated circuit and an antenna, which are used to transmit data to the RFID reader (also called an interrogator).
Chapter 9 -- Network II Flashcards | Quizlet A) Polymorphic malware can change its characteristics every time it is transferred to a new system. B) Polymorphic malware is designed to activate on a particular date, remaining harmless until that time. C) Polymorphic malware is software that disguises itself as a legitimate program, or replaces a legitimate program's code with destructive code.
Network+ 8th Edition Chapter 11, Chapter 10 ... - Quizlet When using DiffServ, what type of forwarding utilizes a minimum departure rate ... An RFID label on a box is an example of what type of physical security ...
Ch 9: Network Risk Management Flashcards Preview - Brainscape An RFID label on a box is an example of what type of physical security detection method? A asset tracking tagging 20 Q What statement regarding the different versions of the SHA hashing algorithm is accurate? A SHA-2 and SHA-3 both support the same hash lengths. 21 Q


















Post a Comment for "40 an rfid label on a box is an example of what type of physical security detection method"